Decentralization is about diversity
By Kenton Varda - 17 Aug 2016
Lately, there has been a flurry of activity around decentralizing the web. Summits have been held. New projects – and companies – have been started. Having worked on this issue for several years now, we’re excited to see it becoming increasingly mainstream.
But what, exactly, are we trying to solve? Most people think it has something to do with privacy, and maybe also security. Some argue that data ownership and mobility are the most important things. Sometimes this leads decentralization projects to focus on data storage while neglecting compute. Some projects even propose that so long as storage is decentralized, it doesn’t matter where the software actually runs.
Privacy, security, ownership, and mobility are all important, but I feel there is a much more important goal that is often poorly understood:
The most important reason to decentralize is software—and developer—diversity.
By “diversity”, I mean this: Who can develop software that other people can plausibly use? Is it primarily mega-corps like Apple and Google? VC-backed startups? Or can one random person, working in their spare time, build just the right app and reach millions of people? Can a community of unfunded volunteers build an open source app that wins because it is the best? Can an employee of one company, having built a useful internal app to solve a problem they had, give (or sell) that app to another company in the same position, without a lot of hassle? Can a teenage fan of a particular video game build an app that assists players of the game, and then share that app with the rest of the game’s community?
All of the above happens regularly with mobile and desktop apps, but it is far more difficult on the web.
We live in a time when our tools are so good that a single competent application developer working weekends can create almost any web application you can imagine. However, rarely can that single developer also run a secure, scalable service and a business around it. As a result, when software is delivered as a service, the only software that is available is that which was deemed a priori to be sufficiently lucrative to interest a mega-corp like Google or a VC-backed startup. Therefore, the only software services we get come courtesy of these gatekeepers. Experimental, indie, or amateur projects are rare. Novel services serving a small niche community are rare. Services designed by people who aren’t well-represented in the tech industry are rare. Community-driven open source projects basically aren’t viable.
The only way to solve these problems is by decentralizing the software (not just the storage). Software must be provided as a package – not as a service – with each user running their own private copy. It doesn’t really matter if the user chooses to deploy to “the cloud” or to their own machine, as long as they can run any package they want. It is, however, important that the means to deploy software be accessible even to non-technical users, so that everyone can participate and developers can reach a wide audience. Deploying an app on your server must therefore be as easy as installing an app on your phone, and must be “secure by default”.
This is the focus of Sandstorm.
Share many as one, with the Collections app
By David Renshaw - 09 Aug 2016
Starting work on a project in Sandstorm often means creating many grains, each pertaining to a different aspect of your work. In a typical project, you might have a spreadsheet, a chat room, a kanban board, and several source code repositories. Sandstorm makes it easy to share these grains with your collaborators, but until recently, you would need to share each grain to each collaborator separately — a task that could quickly become tedious. What if you want to share the entire project as a single unit?
Now that we have released the Collections app, we have a satisfying answer to that question; to share many grains at once, you add them to a collection.
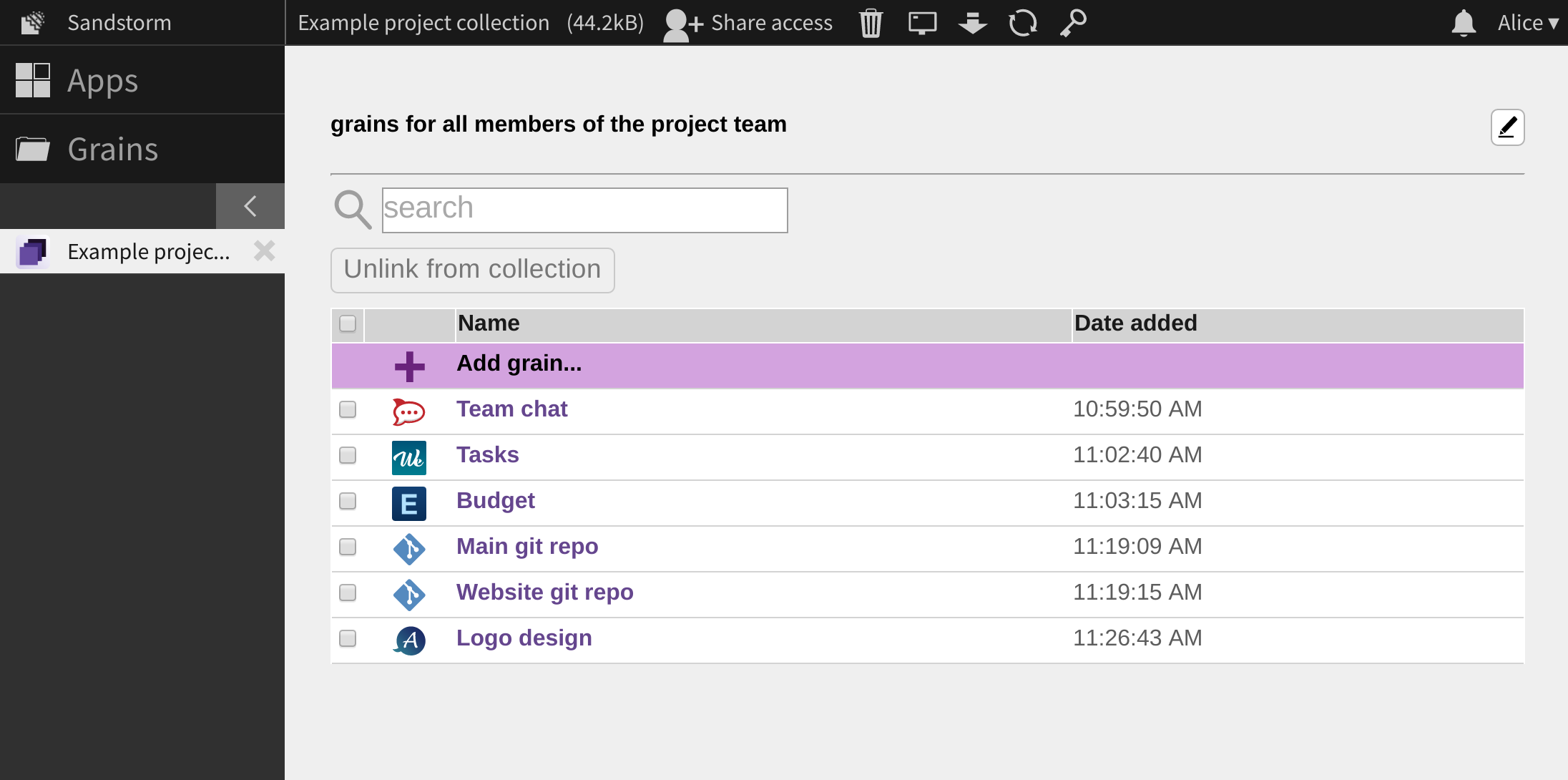
A collection is a list of grains. Any collaborator with whom you share a collection gets access to all of the grains in it. On the flip side, when you remove a grain from the collection, your collaborators lose access to that grain. Moreover, when you revoke a collaborator from the collection, that (now former-) collaborator loses access to all of the collection’s grains.
And since a collection is itself a grain, sharing one works just like sharing anything else on Sandstorm, through the “Share access” button.
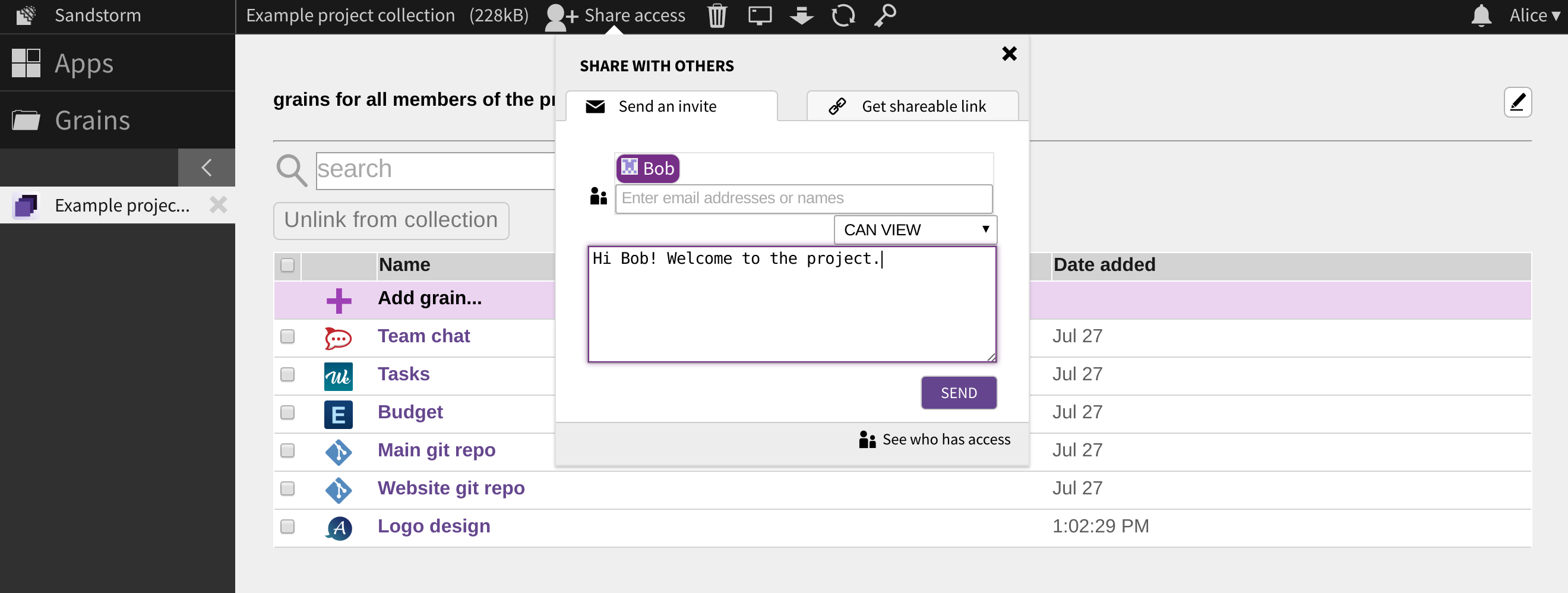
Powerbox makes it possible
The fact that we have implemented collections as an app may come as a surprise, since the notion of a collection might seem fundamental enough to deserve being baked-in as a core feature of Sandstorm. However, Sandstorm bakes in an even more fundamental notion: the idea that grains can refer to and coordinate with one another. The embodiment of this idea is the powerbox, an interface — mediated and auditable by the user — through which grains can exchange capabilities.
When you click the “Add grain” button in a collection, the collection in fact initiates a powerbox request. Sandstorm then asks you, the user, to choose a grain with which to fulfill the request.
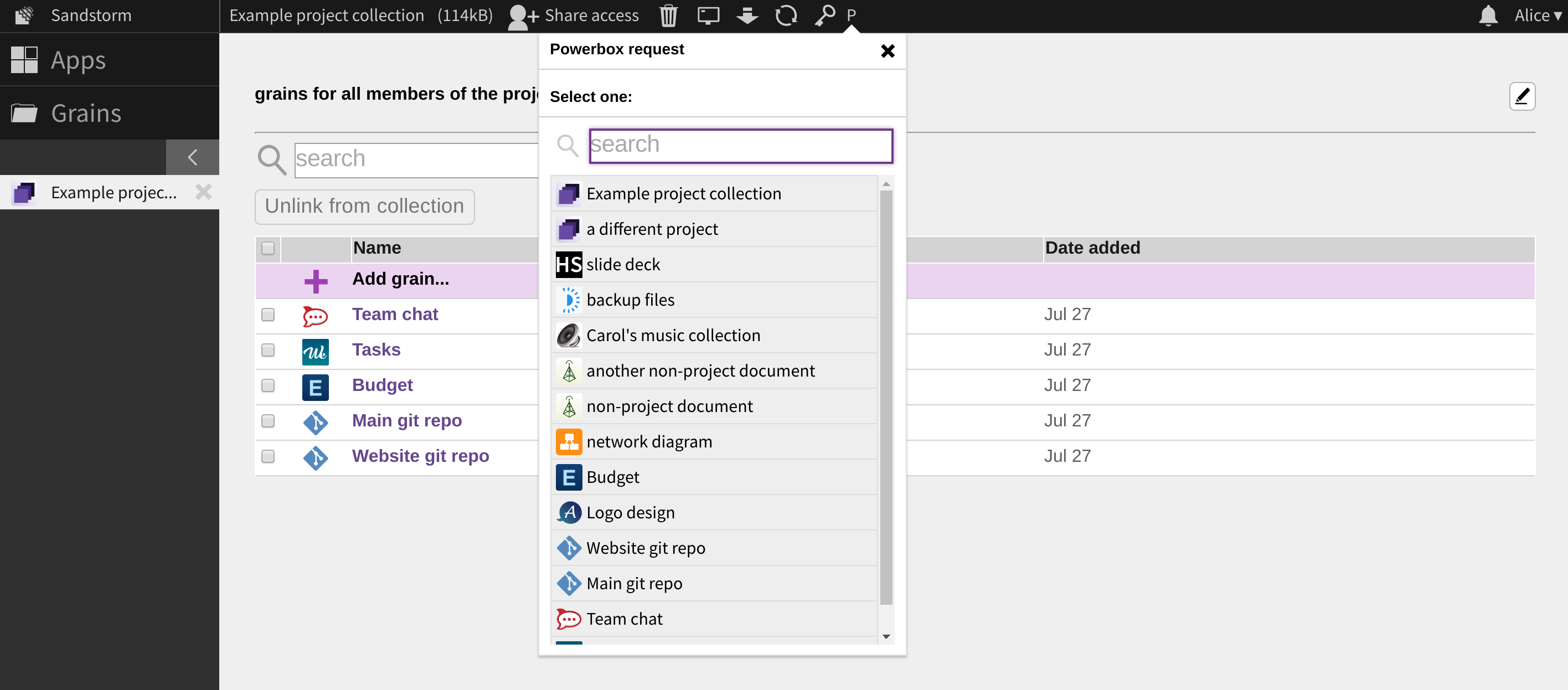
Once you select a grain, the collection receives a reference to that grain. It can then use that reference to retrieve metadata such as the grain’s icon and the the name of the app that created the grain. Crucially, it can also offer the reference to your collaborators, so that your single “Add grain” action can result in all of your collaborators receiving access to the grain. The behind-the-scenes details of how this all works can be found in our technical documentation.
Other apps can use the powerbox in the same way. You could write an alternative implementation of collections, either by starting from scratch or by forking ours. Apps whose primary purpose has nothing to do with collections can also benefit from the ability to request and offer grain references. For example, a chat room could be enhanced by the ability to embed Sandstorm-aware links to other grains. Indeed, the latest release of Rocket.Chat does just that.
Built with Rust
Although a fast startup time and a small memory footprint are important performance goals for any Sandstorm app, they are especially important for the Collections app, as it provides such a central piece of functionality. Collections need to be lightweight so that their integration with the rest of Sandstorm can feel seamless. Our primary strategy for achieving such performance has been to develop the Collections app using the Rust programming language, interfacing directly with Sandstorm’s Cap’n Proto interfaces . Rust has worked well so far, and along the way we have produced some libraries and examples to help others also get started using it for Sandstorm app development.
Whether or not you are a developer, now is an exciting time to get involved with Sandstorm. The powerbox is still in its early stages, and the Collections app is a hint at the kinds of things it will enable. So try it out and let us know what you think!
July changelog - what's new in Sandstorm
By Asheesh Laroia - 03 Aug 2016
In July, we introduced a new Sandstorm feature: Apps can notify users when something interesting happens within a grain. For example, Etherpad uses this to tell you when someone leaves a comment on a document. This ActivityEvent API was designed by Kenton Varda and its visual elements were designed by Néna Nguyễn. You can read more in its Cap’n Proto definition; any app within Sandstorm can use it. The easiest way to try it out is to make a new Etherpad document, then open it in an incognito window, and use the incognito window to leave yourself a comment.
This change, and many more, went live during July. To keep your Sandstorm server updated, you can sit back and relax. In the default configuration, Sandstorm’s automatic updates will install updates within 24 hours of a new release.
Here’s the full July changelog!
v0.173 (2016-07-23)
- Sandstorm for Work: Added server whitelabeling features. Find under “Personalization” in the admin panel.
- Apps now receive profile pictures for all users. Users who have no picture get an identicon. Previously, apps were expected to generate identicons themselves.
- HTTP requests to / responses from apps now pass through any header prefixed with
X-Sandstorm-App-. Also,X-OC-Mtimeis whitelisted in responses, to improve Davros’ compatibility with ownCloud clients. - Attempting to download a backup of a collection will show a warning explaining that this doesn’t do what you expect.
- Prevented guests from uploading grain backups. These uploads weren’t creating actual grains, but could use up server-side disk space.
- Fix bug in grainlist deduplification on app details page.
- Fixed that the admin page for managing a specific user only showed their login identities, not non-login identities. The main list showed both, but the non-login identities would disappear when clicking through to a specific user.
- The favicon is now transparent instead of white-background.
- The guided tour highlight of the “share access” button no longer blacks out the button on Firefox.
- The admin UI’s “Personalization” page no longer fails to save if you haven’t entered a Terms of Service or Privacy Policy URL.
- “204 No Content” responses from apps now preserve the ETag.
- Refactored powerbox client-side code to make it more pluggable.
v0.172 (2016-07-15) [bugfixes]
- Fixed a regression that caused accepting an app update notification to have no effect. Sandstorm will re-notify about missed updates within 24 hours.
- Fixed bugs preventing Sandstorm from working on IE10.
- Tweaked new activity event API.
- Major refactor of powerbox-related code.
- Bugfixes related to upcoming collections app.
v0.171 (2016-07-09)
- Activity/Notifications API: Apps can now inform Sandstorm when a grain has been modified. Sandstorm will then highlight the grain in the user interface to show that it has new content, and in some cases deliver notifications to interested users. Apps need to be updated to use the API, but an update to Etherpad will ship on Sunday with updates to Rocket.Chat and Wekan soon thereafter.
- Fixed regression where grain UIs would not refresh when the grain’s package was updated.
- Fixed bug where it was possible to have a “shared with me” copy of a grain you own show up in your grain list, which in turn caused other bugs.
- Fixed spurious deprecation warning in server logs and reduced the size of the Sandstorm bundle by 10% by eliminating redundant copies of the Connect framework which were being included due to npm dependency semantics.
- Fixed some modal dialogs stretching off the screen on mobile.
- Various code refactoring.
- Oasis: Fixed that save()ing a capability was producing a SturdyRef that could not be restored due to bookkeeping errors.
- Sandstorm for Work: The SAML XML blob is now available even if the SAML identity provider has not yet been enabled. This should make setup easier.
v0.170 (2016-07-02) [bugfixes]
- Meteor-based apps will no longer go into redirect loops when WebSockets are not working.
- Sandstorm for Work: Fixed SAML login failing when a user’s name contained non-ASCII characters.
- The Powerbox API has changed slightly to involve a server-side exchange after the client-side selection operation. This improve security. Existing powerbox-using apps will need to be updated – but no major apps are using it yet.
- When using email login and clicking the link (rather than copy/pasting the token), you will now be redirected back to the URL from which you initiated login.
- Improved design of profile editor UI.
- The user table in the admin panel can now be sorted by clicking column headers.
- Fixed “guided tour” hint bubble for installing apps showing for users who aren’t allowed to install apps.
June changelog - what's new in Sandstorm
By Asheesh Laroia - 13 Jul 2016
June’s big change is that we’ve reworked what first-time users see when using Sandstorm. There are speech bubbles guiding them to install an app, create a grain, and to take a look at the “Share access” interface, all powered by intro.js. I’m hopeful this helps people become productive and comfortable with Sandstorm faster than before.
It applies to all users, including demo users, so test it out by opening demo.sandstorm.io in an incognito window and click Try a quick demo.
Some readers will appreciate that this month, we also chased down a subtle memory leak caused by a lack of flow control in the HTTP implementation spread across proxy.js and sandstorm-http-bridge. You’ll find the details in pull request #2056.
Read the full changelog here, or visit your own Sandstorm server’s “About Sandstorm” section for a changelog at any time.
v0.169 (2016-06-26) [bugfixes]
- Fixed regression in static web publishing that caused requests that should have returned 404s or redirect-to-add-trailing-slash to instead return a 500 status with a blank page.
- Added ability for admin to request a heapdump (to debug memory leaks).
v0.168 (2016-06-24) [bugfixes]
- Sandstorm for Work: SAML connector should now work with Active Directory.
- Fixed various subtle resource leaks in Sandstorm front-end and sandstorm-http-bridge.
- Fixed random crash/hang bug introduced in sandstorm-http-bridge v0.166. Apps build since that time will need to be rebuilt.
- The old admin interface has been completely removed (the new admin interface has been the default since v0.164).
- The email configuration test dialog now shows more informative error messages.
- The “most-used” apps row is now only shown if you have more than 6 apps, without which it isn’t helping.
- Added “guided tour” hint highlighting the “share access” button.
- Added explanatory text to admin user invite page.
- Fixed search bar autofocus on app list page.
- The question mark info button on Grains page was supposed to have a circle around it.
v0.167 (2016-06-18) [bugfixes]
- Updated to Meteor 1.3.3.1.
- Implemented hard flow control at the Cap’n Proto layer so that an errant (or malicious) app cannot cause excessive memory use elsewhere in the system by making excessive simultaneous calls. This should improve the stability of Oasis.
- Implemented flow control for uploads to an app (though it rarely comes into play unless running Sandstorm locally).
- Fixed that after losing internet connectivity for a while (or suspending your laptop) and then coming back, grains would refresh.
- Fixed some memory leaks in shell server.
- Added more “guided tour” points to help new users learn Sandstorm.
- Sandstorm for Work: SAML connector now exports XML auto-configuration blob.
- Sandstorm for Work: Improved UI around feature keys.
v0.166 (2016-06-11) [bugfixes]
- Implemented flow control for large file downloads from apps so that they don’t buffer in the front-end consuming excessive RAM. Apps that handle large files will need to re-pack using the latest sandstorm-http-bridge and push an update.
- Sandstorm for Work: Made SAML entity ID configurable; added more setup instructions.
- Updated Google login setup instructions to match latest gratuitous UI changes.
v0.165 (2016-06-04) [bugfixes]
- Re-enabled websocket self-check under new admin UI.
Upcoming Event: Web app packaging in Sandstorm: It's not LAMP
By Nena Nguyen - 29 Jun 2016
On July 19th, Sandstorm core dev Asheesh Larioa will be giving a talk about web packaging at our South Bay Sandstorm meetup.

Talk details
This talk covers how web app packaging works for Sandstorm.io. Asheesh will compare and contrast Sandstorm packaging against the typical install process on a Linux/Apache/MySQL/PHP system. This talk was featured at Debconf16, the yearly Debian conference.
He will outline how Sandstorm’s packaging tools do a few strange things to allow unprivileged users to install apps with one click:
• Every app package is a tiny Debian derivative, often as small as 20MB.
• Apps have no Internet connectivity to the outside world.
• Sandstorm uses a FUSE filesystem to identify which files are needed to run the app.
• An app bundles all its needed services, as well as files, resulting in one MySQL service per app.
• Users click and run one instance of an app like Etherpad per document, which is all handled transparently via a web app, a strategy that has neutralized 95% of 0-day web app vulnerabilities, based on our analysis.
• Developers on Mac OS and Windows can create packages for Sandstorm, even though Sandstorm is Linux-only, due to an emphasis on Linux VMs in our development tools.
Somehow we manage to make this scale reasonably well. Additionally, it is popular with upstream authors: of the >58 web apps packaged for Sandstorm, about 1/3 are maintained by their upstreams.
This talk focuses on how the Sandstorm packaging tools work, with community insights as well as technical ones, with the hopes of showing Debian how to more effectively package web apps for end users.
Come for the opportunity to meet others in the Sandstorm community, and work on your project with guidance from our core devs. This event will be held at RethinkDB in Mountain View on July 19. RSVP here.